SQL Injection
What is SQL?
SQL is short for Structured Query Language. It is a programming language for querying (fancy word for accessing) and managing databases. SQL is has its own syntax and different database systems some of which include Microsoft Access, SQLite, MySQL, and PostgreSQL. Each of these databases have individual variations of SQL. SQL is essential to web applications that require data storing/access.
SQL Injection
SQL injection primarily involves leaving "windows" open in code for hackers to retrieve data they shouldn't have access to. in the context of Ruby, when strings were not properly closed off with quote marks it led to errors. However, when working with SQL these strings are the open windows in website's databases. The hacks occur whenever the program or website receives input from the user without sanitizing it. For example, if we had a website connected to a database of customers' credit card information the hacker could inject his own SQL statement into the query and take the information he or she wanted. In the figure below a user would input between the quotes in the first line to enter information.
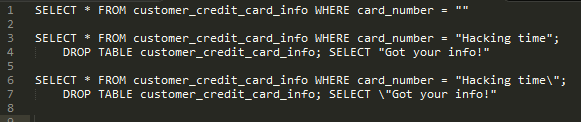
In lines 3-4 a hacker with malicious intentions has inserted his own query into the field and is now taking all information in the customer_credit_card_info table. To sanitize this code we can add escaping backslashes before every first quote mark from the user like in lines 6-7. Now, the query the hacker has inputted returns nothing.
The SQLite3 gem for Ruby has a method for handling the quoted input by using '?' placeholder in the query and passing extra values to the 'execute' method. The number of placeholders must match the number of arguments. This prevents a hacker from adding his own number of arguments in the query.
There are many other methods to prevent SQL injection some of which include the use of Prepared Statements or parametized queries, use of stored procedures, escaping all user supplied input which we discussed above, enforcing least privilege, and white list input validation. Using prepared statements are simple to write and understand. Parametizing queries require SQL code to be defined first and then pass each parameter into the query later. This allows the database to differientiate between code and data regardless od user input. Prepared statements prevent the hacker from changing the intention of the query. For example, if a hacker wanted to input in 'Rick' or '1'='1 the parametized query would deny the hackers' malicious intention and would literally look for the string or for '1'='1. For the sake of blog length you can find the other methods explained in great detail in the links provided below.
For additional information on SQL injection and its prevention methods check these websites out!
Posts
-
The Post DBC Experience
Mixed Emotions
DBC was an awesome, maybe one of a kind experience. I pushed through all 4 phases with the mantids, or the improper plural...
-
How to Ask for Help
How to Ask Good Questions
Experienced Questioning
I don't always ask questions online but when I do I try to be as specific as possible...
-
Ruby on Rails
Rails
Ruby and Rails are not the same thing. Ruby is the programming language. Rails is a Rubygem or package library which is installed via...
-
Resolving Conflicts
A Conflict I Experienced
Honestly, I cannot remember a conflict I've experienced off the top of my head that would be exciting to read or...
- My Thinking Ways How do I Think? I am a concrete sequential thinker which according to cgribben.com mean that I am persistent and product oriented. I am practical...
-
SQL Injection
What is SQL?
SQL is short for Structured Query Language. It is a programming language for querying (fancy word for accessing) and managing databases. SQL...
-
Affirmation and Stereotype Threat
My Values
Accomplishment, accountability, compassion, creativity, efficiency, family, friendships, and integrity area few values which come to mind when I recall the times in my...
-
Blocs, Procs, and Lambdas
Ruby Blocks, Procs, Lambdas
Blocks
A ruby block is the piece of code that is executed. This code can be executed using curly brackets {}...
-
Stereotype Threat
What is Stereotype Threat?
To put it simply, stereotype threat is the experience of not living or carrying out your full potential because of stereotypes....
-
A Pair of Minds
Pairing and Feedback
Pairing
Pairing isn't so bad. The peers are all nice and I haven't met someone who was disrespectful during the sessions. Despite...
-
A Little Ruby
A Snippet into Ruby Classes
When and Why Should I use classes?
One question which kept simmering in my head while working on this week's...
-
Ruby Cycle and Looping
Ruby:Enumberable#Cycle
The #cycle method uses a block for each element of an enumerable object (ranges, hash, or array) repeatedly for n times or endlessly if...
-
Today's Software Apps vs Law
Who Doesn’t Like App Efficiency?
Innovative technologies usually clash with old ways and methods. There are numerous apps out there which are constantly clashing with...
-
What is JS?
What is JavaScript and Why Should You Care?
Javascript(JS) is an object oriented computer programming language often found as a part of web browsers which...
-
CSS Positioning
Positioning in CSS
Elements on a website can be positioned behind, in front of, or next to by using CSS positioning properties: top, left, right,...
-
My Favorite Websites
My 3 Most Visited Websites
Newcelica.org
This is one of my favorite sites because I own a Celica. I do all...
-
Kitchen Vs Table
Kitchen Vs Table
DBC sounds like a buttkicker, a mental, emotional, and physical obstacle course. Honestly, it sounds like it would and should be overwhelming...